
Fake Tokens: Why They Exist and How to Avoid Them
At our crypto exchanger, users sometimes send us tokens that bear the same name as legitimate ones — but in reality, they’re not the real thing. For example, someone looking to swap USDT for USDC might send us a token labeled “USDT.” It looks like USDT in their wallet and in the block explorer, but it wasn’t issued by Tether. It’s a fake.
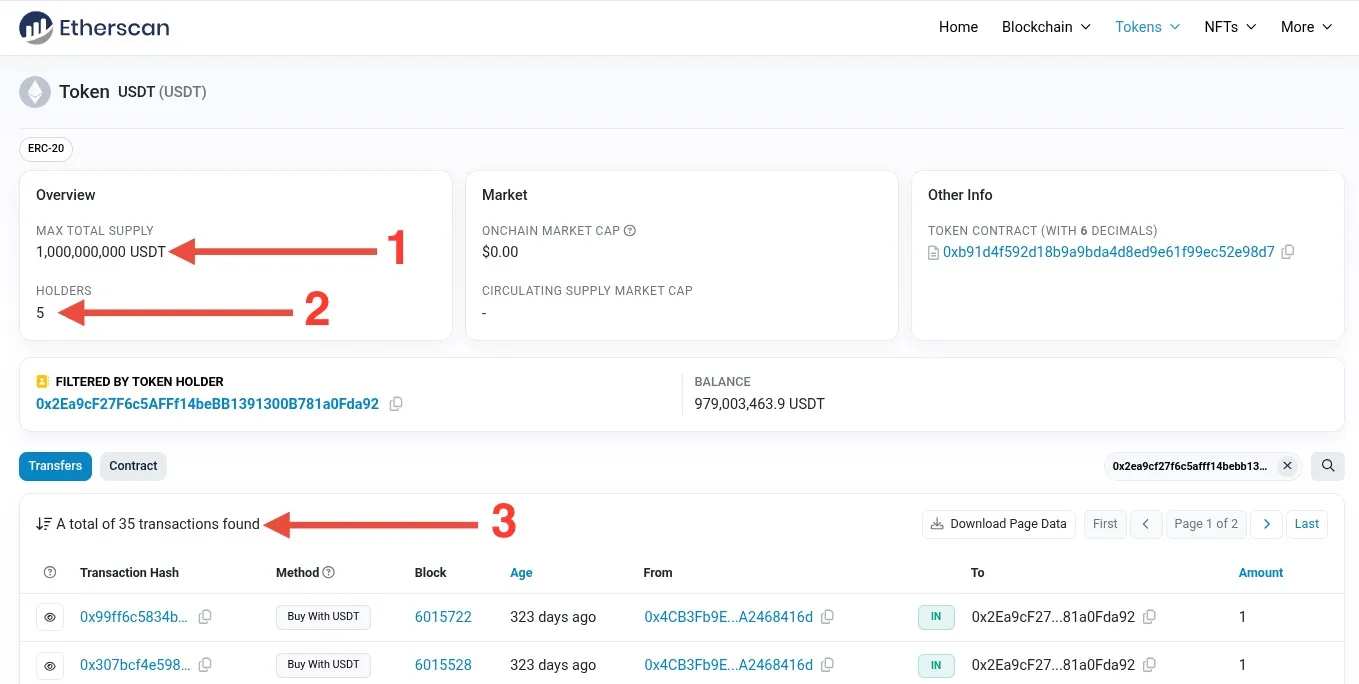
As professionals, we can spot counterfeit tokens right away. In fact, so can any attentive user. For example, in the screenshot above, you can see that the fake USDT token has a total supply of 1 billion tokens[1], all stored across just five addresses[2], and only 35 transactions have ever been made with it[3]. That’s a clear red flag.
But here’s the problem: you’d only notice these details if you actually looked up the token in a block explorer. Most wallets don’t show that kind of information — they just display the token’s name (e.g., USDT) and your balance. So users often have no idea they’re dealing with a fake. They received it from someone, assumed it was real, and went on with their business.
It’s always painful when our support team has to break the news that a token is worthless — especially when the amount involved is large. Some users refuse to believe it at first. For them, those 50,000 “USDT” tokens were equivalent to $50,000… until we told them otherwise.
In this article, I want to explore why this happens — and whether there’s anything that can be done about it.
Why Are Fake Tokens Created?
Most blockchains are completely open systems. Anyone can write anything into them — including creating a token with any name they like. There’s no central authority to prevent someone from registering a token called “USDT” or “Bitcoin.” On the one hand, that’s a strength: the network resists censorship. But on the other hand, it means that dozens of tokens with identical names can coexist in the same ecosystem.
This problem became especially noticeable during the ICO and DeFi booms on Ethereum. On platforms like Uniswap, anyone could list a token, and scammers quickly took advantage of that. One of the first high-profile examples was the token sale of Polkastarter (POLS) in September 2020. The price of the token skyrocketed immediately after the launch, and scammers rushed to issue fake POLS tokens and list them on Uniswap.

While the real token had a distinct logo on Uniswap, that didn’t stop some users from buying the fakes. One of them was purchased for over $30,000.
In many wallet interfaces, it was even worse: the fake tokens looked exactly like the real ones. Some wallets didn’t display logos at all. Others pulled them from external sources — and scammers simply uploaded the Polkastarter logo to make their fake token appear authentic.
In some cases, confusion doesn’t even require identical names — just shared tickers. For example, when Uniswap launched its token UNI, some traders confused it with another token also called UNI — from a project named Unicorn. People rushed to buy the wrong token, pumping its price from $0.001 to $5 — a 5,000x increase. Once the mistake was realized, the price crashed just as quickly. Some made money by accident, others lost theirs just as easily.
There are also cases where a token mimics not another token, but the name of a crypto service that doesn’t even have a token. A rumor spreads: “It’s the real token of the project, but they haven’t officially announced it yet — that’s why it’s still so cheap!” For instance, in January 2025, the startup SoSoValue warned that someone had issued a fake SOSO token on BSC using their brand — even though they had never launched any cryptocurrency. Users were urged to avoid the fake and verify sources of information carefully.
Once you’ve bought a fake token, chances are you won’t be able to sell it — unless you trick someone else into believing it’s real. Still, oddly enough, fake tokens sometimes do attract demand. For example:
- On February 13, 2025, Changpeng Zhao posted a picture of his dog Broccoli on X and explicitly stated that he was not going to issue any token in her name. Nonetheless, several “Broccoli” tokens popped up on BNB Chain, and some of them are still being traded — and swapped on rabbit.io.
- On March 12, 2025, a fake PAWS token was trading on the Raydium DEX at 90 times the price of the real PAWS token on Bybit.
The truth is: attention creates value — even for knockoffs. And some counterfeiters are very good at attracting attention to their creations.
Still, this isn’t something you should count on. If you’ve received a fake token, I strongly recommend not trying to figure out where you might be able to dump it.
Back in 2021, scammers on the Tron blockchain sent out free tokens to thousands of addresses. These tokens often had flashy names mimicking real cryptocurrencies. When unsuspecting users found the “gift” in their wallets and tried to sell it, they were lured into a trap: the only platform where the token appeared tradeable prompted them to approve a suspicious smart contract — which could compromise their wallets.
That particular scheme is mostly forgotten now. But I worry that scammers might be tempted to repeat it on some other blockchain where token distribution to thousands of wallets is cheap and easy.
Can the Fake Token Problem Be Solved?
There are, in fact, technical solutions.
The first tokenization protocols — Colored Coins, Omni Layer, and Counterparty — were introduced between 2012 and 2014 and built on top of the Bitcoin blockchain. Colored Coins and Omni Layer placed no restrictions on using the same token name multiple times. In contrast, Counterparty introduced a system where token names must be unique. That means if someone created an asset called LTBCOIN in 2014, and you see a token with that name today in 2025, you can be confident it’s the same token. The protocol verifies whether the chosen name has already been registered. If it has, the token creation transaction is rejected.
But this approach never caught on widely. The history of domain names — which operate on the same principle — shows why: attractive names are quickly snatched up, and real project names are often reserved by cybersquatters who have nothing to do with the actual project. So you can still end up with fake tokens, unless the legitimate project’s creators rush to claim their name across all token platforms. Perhaps that’s why Counterparty’s solution hasn’t been adopted by any of the major tokenization ecosystems — not Ethereum, not Solana, not BNB Chain, nor any others.
An interesting refinement of this idea can be seen in the Runes protocol, launched on Bitcoin in April 2024. Every token issued through Runes has a unique name — but names like USDT or USDC are not currently available.
At launch, when the protocol was still under the radar, users were only allowed to register names that were 13 characters or longer. Registration opened at Bitcoin block 840,000 (mined April 20, 2024), and that length restriction was in place for 17,500 blocks. Starting at block 857,500 (mined August 19, 2024), 12-character names became available. Block 875,000 unlocked 11-character names.
Four-character names — like USDT and USDC — are expected to become available around April 2027. The protocol’s developers hope that by then, it will have gained enough traction that real token issuers will be paying attention and will claim their rightful names before squatters do.
However, a year after the launch of the Runes protocol, it seems that it hasn’t really gained traction. Most token creators still prefer other platforms — ones that are cheaper and easier to use. Unfortunately, those platforms offer no protocol-level protection against fake tokens.
Since protocol-level safeguards are rare, developers have started implementing solutions at the application level — in block explorers, wallets, and token lists.
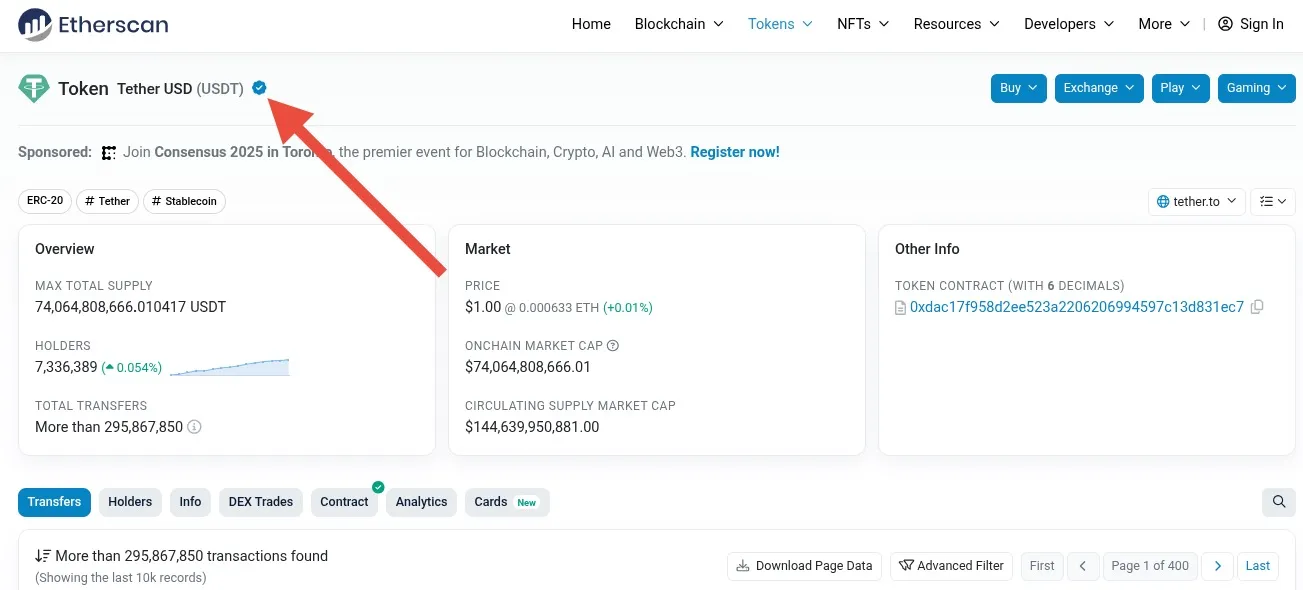
On popular explorers like Etherscan, BscScan, and TronScan, verified tokens are marked with a checkmark or other visual indicators. If a token doesn’t have such a mark, users are advised to proceed with caution.
Wallets — like MetaMask, wallet.rabbit.io, and others — typically display balances only for approved tokens or those the user has interacted with before. Fake tokens that randomly appear in your wallet won’t even show up by default. In MetaMask, users can manually add any token — but to do so, they need to enter its smart contract address, which already encourages them to look deeper than just the token name. That step alone can help users identify a fake.
However, these so-called “whitelists” create a new challenge: they make it harder for legitimate but lesser-known tokens to reach users. Without recognition or verification, newer tokens struggle to get noticed — even if they’re completely safe.
An alternative is to use blacklists — lists of suspicious or misleading tokens. But those come with their own problems. For example, in 2019, the Waves network began blacklisting questionable tokens. One unfortunate case involved HBTC (Humboldt Bitcoin) — a local community token. After several months of active circulation, it was suddenly flagged as spam simply because its ticker, HBTC, seemed to be too similar to BTC. As a result, users who received the token could no longer see it in their wallets — even though the token wasn’t fraudulent and its creators had done nothing wrong.
Some developers are proposing a new format for unified token locators (UTL) — inspired by how URLs work on the web. Instead of identifying a token by its name, the idea is to use a combination of network + token ID to eliminate ambiguity. For example:
- ethereum:0xa0b86991c6218b36c1d19d4a2e9eb0ce3606eb48
- solana:EPjFWdd5AufqSSqeM2qN1xzybapC8G4wEGGkZwyTDt1v
- stellar:USDC-GA5ZSEJYB37JRC5AVCIA5MOP4RHTM335X2KGX3IHOJAPP5RE34K4KZVN
It’s a simple idea with big potential. Just like each website has:
- A name (e.g., Medium)
- And a URL (e.g., https://medium.com)
…tokens could have:
- A name (e.g., USD Coin)
- And one or more UTLs, clearly pointing to the actual asset in a specific blockchain.
This would not only help prevent fake tokens, but also reduce mistakes like sending tokens to the wrong network — something we occasionally see at Rabbit Swap, too. For instance, a user might intend to exchange USDT on Ethereum for BTC, but accidentally sends USDT on Base instead. In such cases, the swap or refund has to be processed manually, which takes far more time than our usual automated workflows.
That said, UTLs — at least in their current form — don’t solve the problem entirely. The part after the colon (the token ID) is indeed unique. But what about the part before it?
What’s to stop someone from launching a new blockchain and calling it “Ethereum,” “Solana,” or even “Bitcoin”? Technically, nothing. And yes, that’s already happened.
In August 2017, the Bitcoin network underwent a hard fork that resulted in Bitcoin Cash (BCH). For a time, during late 2017 and early 2018, the website bitcoin.com promoted Bitcoin Cash as the “real” Bitcoin — while referring to the original chain as “Bitcoin Core” (after its node software). Many users were confused by the branding and ended up buying BCH, thinking it was the original BTC. After widespread criticism, the site eventually walked back that messaging — but the episode proves that even the most well-known cryptocurrencies are vulnerable to impersonation.
And Ethereum? The situation’s no better. To this day, some people still believe that Ethereum Classic is the real Ethereum. So what chain do you think they’re referring to if they give you a UTL like ethereum:0xa0…?
All in all, despite the abundance of technical solutions, the fake token problem isn’t going anywhere anytime soon.
So What Can You Do?
Ultimately, the only real protection is to personally keep an eye on every token that enters your wallet.

If you’ve received tokens as part of a swap made on rabbit.io, you can be confident they’re genuine.
But if tokens come from an unknown source, the best way to stay safe is to use a wallet that only displays verified tokens or those you’ve interacted with before. And before using a new token, make sure to confirm either:
- the smart contract address (for blockchains like Ethereum, Tron, or Solana), or
- the asset ID (for blockchains like Bitcoin, Stellar, or Avalanche X-Chain)
via the project’s official channels or community.
Then, add the token to your wallet manually using that verified address or identifier.
That way, any imitation token — no matter how similar the name — simply won’t show up in your wallet.













