How to Steal Cryptocurrency
If you ask me to name the strongest argument for keeping savings in cryptocurrency, I would say this: Cryptocurrency is the only asset that no one can take away from me without my consent.
- If I keep my savings in a bank, some authority could force the bank to withhold my funds, and the bank would have to comply.
- If I hide cash in a stash, a thief could find it and take it all.
- If I carry cash with me, it could be confiscated by the state or stolen by a robber.
This is not possible with cryptocurrency stored on the blockchain.
- No one can prohibit me from spending my cryptocurrency.
- The blockchain is not a stash; all my funds are visible to everyone, but for a thief to steal them, they would need to sign the transaction with a private key that only I know.
- Private keys are intangible, making confiscation very challenging.
Even when courts issue orders to “forfeit one’s interest in a cryptocurrency wallet,” enforcing such rulings is tricky. The person targeted may simply claim they don’t remember the private key.
At first glance, it seems the only way to take someone’s cryptocurrency is through direct violence (robbery, torture, etc.). Unfortunately, there are other ways.
Not All Cryptocurrencies Are Equal
In certain cases, the use of crypto assets can indeed be restricted.
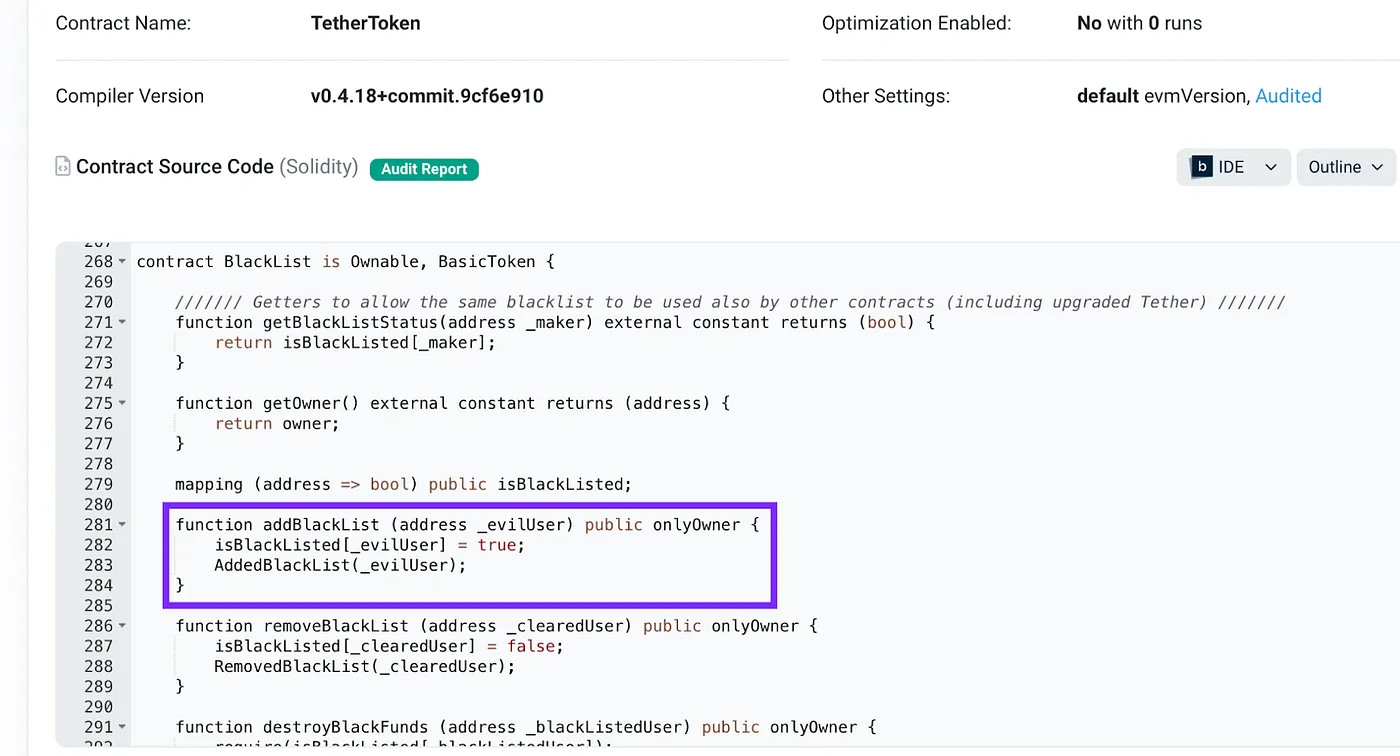
This primarily concerns tokens issued via smart contracts. A smart contract can grant the token issuer authority to block certain addresses from using the tokens. If I attempt to send tokens from a blacklisted address, the transaction won’t be validated and won’t make it to the blockchain because it would violate the smart contract rules.

Source: Etherscan.io
The most notable example of tokens that can be blocked by the issuer are those issued by Tether (USDT, EURT, and others). Smart contracts for these tokens often allow Tether to prohibit transactions from blacklisted addresses. Blockchain data shows that Tether frequently uses this feature.
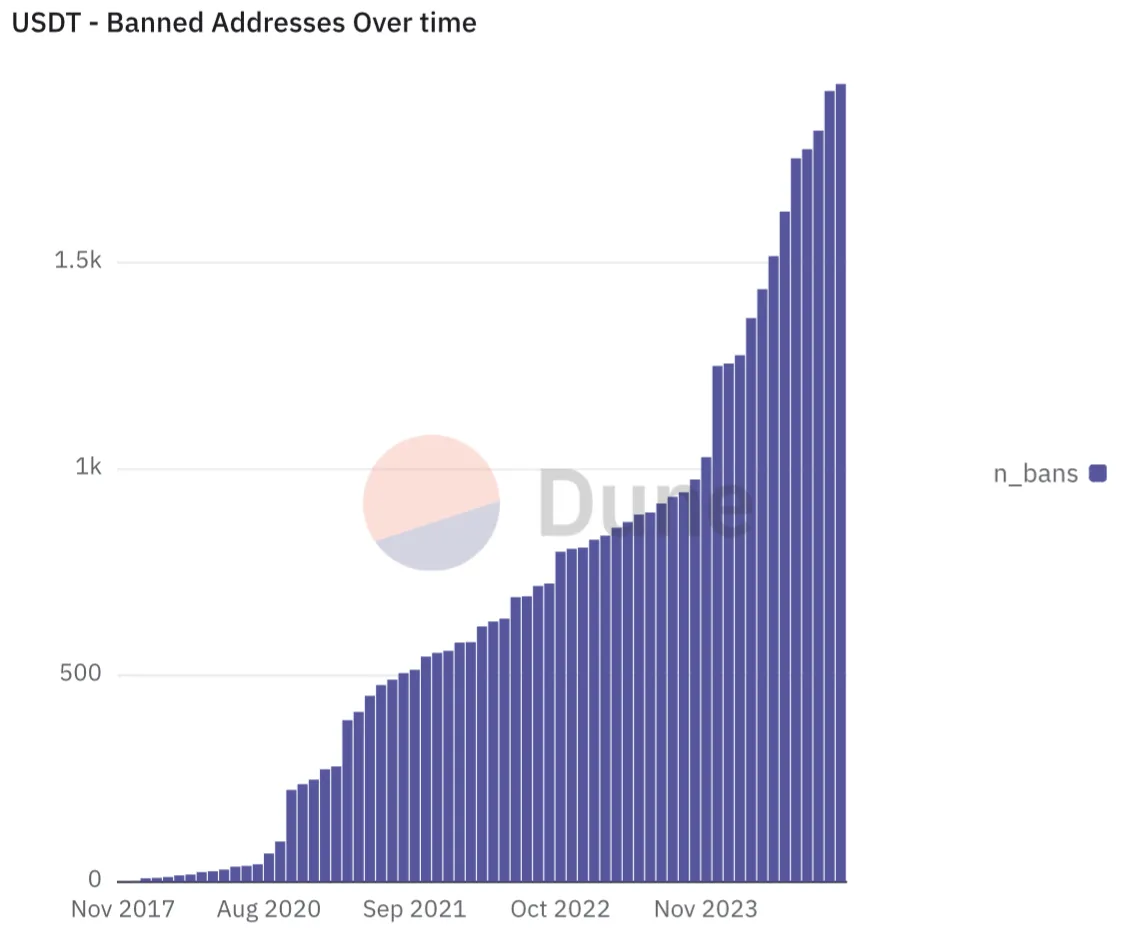
Source: Dune.com
Restrictions can also apply to cryptocurrencies that are not tokens but the native coins of a blockchain controlled by a centralized group. If this group dislikes a transaction, they can take steps to remove it from the blockchain, preventing the recipient from accessing the funds.
Here are some historical examples:
- In 2016, this happened with a transaction in which major investors in The DAO lost 3.6 million ETH. A few weeks later, the Ethereum Foundation, which makes all strategic decisions regarding the Ethereum blockchain, implemented a hard fork that erased the record of this transaction from the blockchain. As a result, the new owner of the 3.6 million ETH lost access to their funds.
- In 2019, the largest mining pools, BTC.com and BTC.top, worked together to reverse transactions that had transferred Bitcoin Cash coins from “Anyone Can Spend” addresses to key-protected addresses. Essentially, someone discovered coins that, under network rules, were ownerless and claimed them. However, the major miners prevented this individual from using their find, reclaiming the coins and taking them back.
- Even the primary Bitcoin blockchain was reorganized at one point (back when Satoshi Nakamoto was actively involved in its development and most developers followed his decisions). On August 16, 2010, Satoshi published a patch for Bitcoin’s main client on the Bitcointalk forum. The purpose of this patch was to remove a block from the blockchain that contained transactions generating an excessive number of bitcoins. The owner (or owners) of the generated bitcoins were thereby deprived of the ability to use their coins.
In these examples, we see not just a prohibition on the use of coins but an outright reversal of transactions. This mechanism exists in almost all blockchains and is commonly referred to as a “51% attack”:
- In Proof-of-Work (PoW) systems, an attacker who controls more than 50% of the network’s computational power can mine two competing versions of a block at the same height, invalidating earlier transactions.
- In Proof-of-Stake (PoS) systems, a similar attack can occur if the majority of staked coins are controlled by a small, centralized group.
Thus,
- if a PoW blockchain lacks sufficient overall computational power in the network,
- or if, in a PoS blockchain, the majority of coins are not owned by those who purchased them at market value but by initial holders who acquired them for free or at a low cost,
then in such a blockchain, you might receive cryptocurrency only to later find that the transaction through which you received it has been reversed. As a result, your cryptocurrency might still belong to its previous owner or could have already been transferred to someone else (in other words, effectively stolen from you).
Can Cryptocurrency Be Stolen Through Hacking?
Media reports frequently detail cases where large cryptocurrency wallets are hacked and funds stolen. This suggests that even robustly designed cryptocurrencies can be targeted if hackers access private keys or seed phrases.
The safest way to protect these is not to store them on internet-connected devices. But even memorizing your seed phrase has risks; skilled social engineers could manipulate you into revealing it. A better approach is to record the phrase physically (on paper, plastic, or metal), split it into several parts, and store them separately. This minimizes the risk of cyberattacks.
However, this level of protection makes frequent transactions inconvenient. To use your cryptocurrency, you often need to rely on devices connected to the internet, which are inherently vulnerable. If you regularly transact with cryptocurrency, ensure these devices are secured to the highest standard.
Web3 Wallet Risks
The Web3 paradigm suggests wallets should be used as universal identifiers for online services. I strongly advise against using wallets containing significant funds for such purposes. Use an empty wallet, or at most, one with a small amount you’re prepared to lose.
Source: Quantumtemple.xyz
The idea of using wallets for authentication is flawed: imagine showing your physical wallet to every organization you enter, allowing them to browse through it. This undermines financial security and exposes you to unnecessary risks.
The Simplest Way to Steal Cryptocurrency
As long as cryptocurrency is stored securely on a reliable blockchain, in an address whose private key you never reveal or display, its safety is virtually guaranteed. Stealing or otherwise taking such cryptocurrency is exceedingly difficult.
It is, of course, possible for someone to convince a cryptocurrency owner to disclose their private key or seed phrase. Such cases do happen, but they require highly advanced social engineering skills.
A much simpler method is not to steal the private key but to trick the owner into transferring the cryptocurrency itself. This can be as easy as promising to provide something in exchange — another cryptocurrency, fiat money, goods, or services — and then failing to deliver on that promise. Once the cryptocurrency is sent to the scammer’s address, retrieving it becomes just as difficult as it would have been to steal it from the original address. In other words, it is practically impossible, provided the scammer follows basic measures to protect against hacking.
This is precisely why cryptocurrencies are inconvenient as a means of payment. Visa, Mastercard, PayPal, and other payment systems have accustomed us to the idea that we can file a complaint against a fraudulent seller, and if the fraud is confirmed, the transaction will be reversed. With cryptocurrency, this is impossible. No one can deprive the recipient who deceived the sender of the cryptocurrency they received. The only exception might be another scammer, who promises something in exchange, only to provide nothing after obtaining the cryptocurrency.
Practical Tips for Using Cryptocurrency Securely
- Choose Your Cryptocurrency Wisely: Opt for cryptocurrencies that:
- Don’t allow blocking via smart contracts.
- Operate on decentralized blockchains, minimizing the risk of transaction reversals.
- Use PoW with substantial computational power or PoS where all stake owners purchased their coins on the open market rather than receiving them for free or at negligible cost.
- Secure Your Private Keys: Most crypto theft occurs due to user errors, such as weak passwords, clicking on phishing links, or mishandling private keys. Always safeguard your keys — they are the sole means of owning your cryptocurrency.
- Be Careful with Transactions: Only send cryptocurrency to trusted parties. If a deal seems too good to be true, it probably is. Unlike traditional payment methods, crypto transactions are irreversible, leaving you vulnerable to scams.
At Rabbit Swap, we know from experience that the most vulnerable aspect of using cryptocurrency is exchanges — our area of expertise. When exchanging or purchasing anything with cryptocurrency, only deal with reliable and trustworthy parties.
On our platform, we offer fair and competitive exchange rates. However, if you encounter suspiciously advantageous offers elsewhere, exercise caution. Once your cryptocurrency is sent, it cannot be recovered in cases of fraud.
Stay vigilant, trade securely, and rely on trusted platforms like Rabbit Swap for all your exchange needs. Visit Rabbit Swap for the best exchange rates.













